在CentOS 7.2系统中利用Certbot工具配置Let's Encrypt通配符证书,所域名下所有的子域名都能方便的使用 https证书,而且完全免费。值得关注的是,Let's encrypt通配符证书只是针对二级域名,并不能针对主域名,如*.example.com和example.com被认为是两个域名,如果和我一样使用的是主域名,在申请的时候需要注意都要申请。
获取Certbot
# 下载
wget https://dl.eff.org/certbot-auto
# 设为可执行权限
chmod u+x certbot-auto
申请证书
执行以下命令
./certbot-auto certonly -d "*.example.com" -d "example.com" --manual --preferred-challenges dns-01 --server https://acme-v02.api.letsencrypt.org/directory
参数说明:
-certonly表示安装模式,Certbot 有安装模式和验证模式两种类型的插件。-manual表示手动安装插件,Certbot 有很多插件,不同的插件都可以申请证书,用户可以根据需要自行选择。-d为哪些主机申请证书,如果是通配符,输入 *.example.com(替换为自己的域名)。-preferred-challenges使用 DNS 方式校验域名所有权。-serverLet’s Encrypt ACME v2 版本使用的服务器不同于 v1 版本,需要显示指定。
注意将example.com替换为自己的域名
执行过程中确认以下信息
Plugins selected: Authenticator manual, Installer None
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): test@example.net
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Obtaining a new certificate
Performing the following challenges:
dns-01 challenge for example.com
dns-01 challenge for example.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
NOTE: The IP of this machine will be publicly logged as having requested this
certificate. If you're running certbot in manual mode on a machine that is not
your server, please ensure you're okay with that.
Are you OK with your IP being logged?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
在域名 DNS 解析中添加 TXT记录
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.example.com with the following value:
c1tiuYabTeauuA3Byjc6Sdn7vbBPjwXZkdZDnry5wvg
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
接下来需要到域名服务器商添加两条TXT记录,本人使用的是腾讯云,以下是解析记录
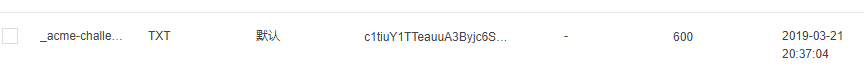
添加以后会有最多10分钟的生效时间,这里先要确认解析已经生效,才能在配置Let's Encrypt的终端按回车。
判断解析已经生效,可使用dig _acme-challenge.example.com txt,若出现DNS解析的记录值,则说明解析已经生效了。如下所示:
[root@VM_0_15_centos ~]# dig _acme-challenge.example.com txt
; <<>> DiG 9.9.4-RedHat-9.9.4-50.el7_3.1 <<>> _acme-challenge.example.com txt
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48247
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;_acme-challenge.example.com. IN TXT
;; ANSWER SECTION:
_acme-challenge.xj10.xyz. 600 IN TXT "c1tiuYabTeauuA3Byjc6Sdn7vbBPjwXZkdZDnry5wvg"
;; Query time: 296 msec
;; SERVER: 183.60.83.19#53(183.60.83.19)
;; WHEN: Thu Mar 21 20:39:09 CST 2019
;; MSG SIZE rcvd: 109
确认生效后回车后会让继续添加另一条TXT记录,生效后再次回车:
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/example.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/example.com/privkey.pem
Your cert will expire on 2019-06-19. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
生成的文件在/etc/letsencrypt/live/example.com/目录中
在Nginx中配置证书
在nginx中进行如下配置:
#http跳转至https
server {
listen 80;
server_name example.com;
rewrite ^(.*)$ https://$host$1 permanent;
}
server {
listen 443 http2 ssl;
server_name example.com;
ssl on;
ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/example.com/chain.pem;
location / {
proxy_pass http://127.0.0.1:8080/;
proxy_set_header Host $host:$server_port;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Remote_Addr $remote_addr;
}
}
证书更新
Let's Encrypt 的免费证书默认有效期为 90 天,到期后如果要续期可以执行:
certbot-auto renew
可以定义crontab每晚自动执行
# 每月的 1,15号, 2点30 更新证书
30 2 1,15 * * /path/to/certbot-auto renew
# 每月的 1,15号, 3点30 重新加载配置
30 3 1,15 * * nginx -s reload
